How to Secure Google Tag Manager: Best Practices to Protect Your Tags and Prevent Ad Fraud

Google Tag Manager (GTM) is a powerful tool for managing tracking tags, analytics scripts, and marketing pixels. It gives marketing teams more control over website tagging without requiring constant developer help. This flexibility saves time and improves workflows. However, it also creates serious security risks if not configured properly.
When you use GTM, you’re essentially letting JavaScript run on your website through the browser. If someone injects malicious code into your container, they can steal data, hijack user sessions, or insert fraudulent ads. Many businesses overlook GTM security, granting too much access, skipping audits, or failing to monitor changes. These mistakes leave their websites vulnerable to attacks. In recent years, attackers have increasingly used unsecured GTM containers to spread malware, leak sensitive data, and defraud advertisers.
GTM security is no longer just a best practice. It’s a necessity. Every organization that relies on GTM should take steps to secure it. Poor security can harm your users, damage your reputation, and even lead to regulatory penalties under laws like GDPR and CCPA. It can also cost you money by enabling ad fraud and skewing analytics data.
This guide will show you how to secure Google Tag Manager step by step. You’ll learn why security matters, how to control access properly, and what technical measures strengthen your defenses. We’ll also explain how attackers exploit GTM for ad fraud, and how tools like Spider AF and the upcoming Spider SiteScan help you monitor your containers, uncover hidden risks, and block fraudulent activity.
By the end, you’ll have a clear checklist of actions you can take right away. You’ll also understand how to keep improving your GTM security over time. Let’s begin.
Why Securing Google Tag Manager Is Critical

Google Tag Manager is convenient, but convenience often comes with risk. Many businesses underestimate how much access GTM has to their website and user data. Without proper security controls, your GTM container can become an easy target for attackers. Understanding the risks helps you see why securing GTM should be a top priority for your team.
Common vulnerabilities of GTM containers
GTM containers have several common weaknesses. The most obvious is excessive user access. Too many users with edit or publish rights increases the chance of accidental errors or intentional abuse. Attackers can also exploit weak account credentials if you don’t enforce strong passwords or multi-factor authentication.
Another vulnerability comes from unmonitored tags. Once a tag is added, it stays active unless someone removes it. That means malicious code or old third-party scripts can sit in your container indefinitely. GTM doesn’t automatically warn you about suspicious tags or unexpected changes.
This is where tools like Spider SiteScan can help. SiteScan performs a full inventory of scripts running on your site — including outdated jQuery, residual GTM test tags, and unauthorized no-code tools — and visualizes where hidden risks live. Regular scans can uncover vulnerabilities you might have missed through manual audits.
Real-world risks: data leaks, malicious tags, and ad fraud
Attackers often use unsecured GTM containers to steal sensitive information. For example, a compromised tag can collect login credentials, credit card numbers, or personal details from your site’s forms. These data leaks can trigger regulatory investigations and lawsuits. (If you want to learn more about the real-world risks third-party scripts and compromised tags can pose, check out our article Understanding Third-Party Script Risks
Malicious tags can also redirect visitors to phishing pages or load malware onto their devices. This damages your reputation and can lead to blacklisting by browsers and search engines.
Another growing problem is ad fraud. Fraudsters inject hidden ads or tracking pixels into GTM containers. These fake impressions and clicks drain your advertising budget and distort your campaign data. Businesses have lost millions to such schemes. That’s why pairing GTM security with Spider AF and leveraging SiteScan’s real-time threat monitoring is so important. Together, they actively detect fraudulent scripts, expose unauthorized activity, and help you block bad actors before they cause harm.
How to Lock Down GTM Account and Container Permissions
Controlling who can access your GTM account and containers is the first step to securing them. Poor permission management is one of the most common mistakes teams make. Follow these best practices to keep your GTM environment safe and under control.
Set appropriate user roles and minimize access
Always assign the least amount of access needed for each user to do their job. GTM provides four roles: No Access, Read, Edit, and Publish. Only trusted team members should have Publish rights, and even then, keep the number as low as possible. Give external vendors only temporary or Read access if possible. Review your account’s user list and remove anyone who no longer needs access.
Enable two-factor authentication (2FA) for all users
Strong passwords alone aren’t enough. Enforce two-factor authentication (2FA) for every account that can access GTM. Since GTM is part of the broader Google ecosystem, enabling 2FA on Google accounts automatically protects GTM too.
Review and audit user access regularly
Permissions shouldn’t be set once and forgotten. Schedule audits of GTM user access at least every quarter. Remove accounts for employees who have left the company, and adjust permissions for users who have changed roles.
Implement Technical Measures to Protect GTM
Even with strong access controls, technical safeguards are essential to prevent misuse of your GTM setup.
Use Content Security Policy (CSP) to limit tag behavior
A properly configured Content Security Policy (CSP) can restrict what scripts your site is allowed to load. By defining which domains are trusted, you prevent unauthorized tags from loading malicious code.
Version control and approval workflows for container changes
Always use GTM’s built-in version control and approval features. Encourage your team to label versions clearly and separate editing from publishing duties.
Monitor audit logs to detect suspicious activity
Make it a habit to review GTM’s activity history regularly. Look for unusual activity or unexpected changes. Here, Spider SiteScan can supplement your manual reviews with real-time alerts about unauthorized script changes and anomalies, making it easier for both marketing and security teams to respond quickly.
How to Detect and Prevent Ad Fraud Through GTM
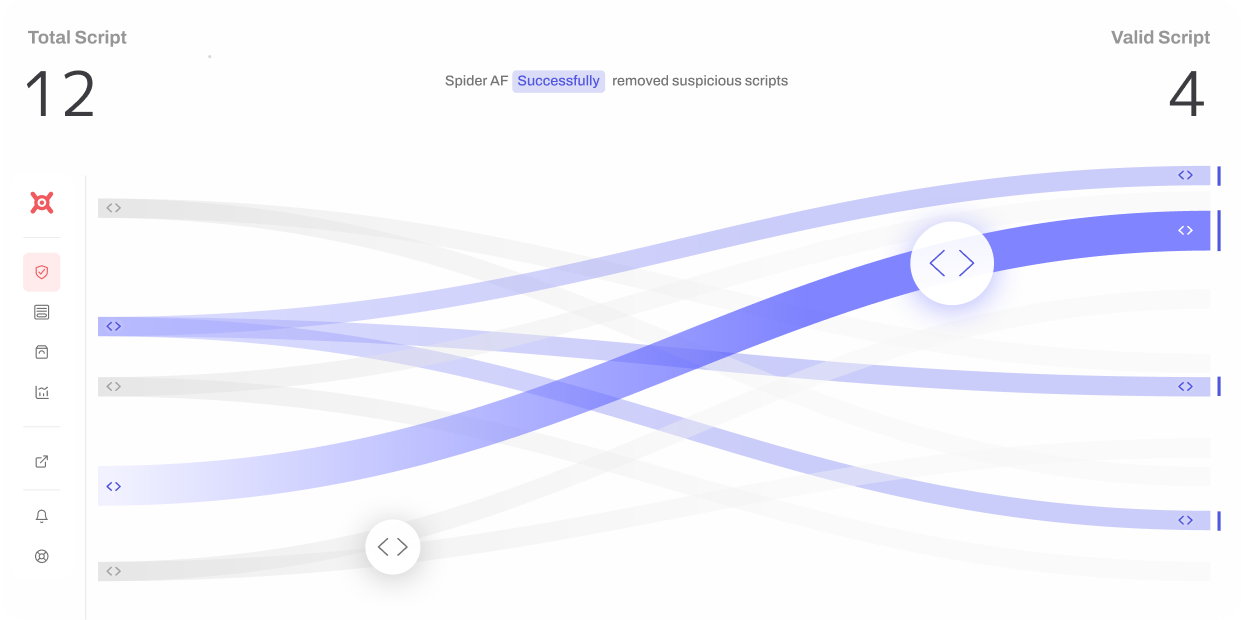
Google Tag Manager is sometimes exploited as a channel for ad fraud.
Why GTM can be exploited for fraudulent ad injections
Since GTM executes JavaScript on your site, any tag you publish runs in your visitors’ browsers. If attackers gain access to your container, they can insert hidden ads or tracking pixels that your team never authorized.
How Spider AF and SiteScan help you monitor GTM and block ad fraud
Spider AF specializes in detecting fraudulent traffic and blocking invalid clicks before they waste your budget. Meanwhile, Spider SiteScan gives you a clear inventory of every script running on your site and flags risky behavior immediately. The combination gives you both proactive fraud prevention and ongoing visibility into your GTM and script environment.
To start detecting ad fraud automatically, you can sign up for a free 14-day trial of Spider AF here. There's no credit card required, and the entire process is quick and simple ( it only takes about 3 minutes from start to finish!).
Advanced Tips for High-Security Environments
For highly regulated or sensitive environments, more stringent practices are necessary.
Secure GTM on highly restricted or regulated websites
Evaluate whether GTM is appropriate for sensitive pages. If used, limit third-party tags and run all changes through a staging environment for compliance checks.
Integrate GTM security with your organization’s overall cybersecurity policies
Work with your security team to include GTM in regular audits and incident response plans. Use tools like Spider SiteScan to generate detailed logs, demonstrate PCI DSS 4.0.1 compliance, and maintain a complete audit trail of script changes.
Final Checklist: Steps You Can Take Today
Here’s a quick reference to secure GTM and keep improving over time.
Quick wins to secure your GTM immediately
Long-term monitoring and continuous improvement
- Schedule quarterly reviews of users and tags.
- Integrate GTM into your security policies.
- Train your team on GTM security risks.
- Deploy Spider AF to block ad fraud.
- Use Spider SiteScan for ongoing script monitoring, real-time alerts, and compliance reporting.
Want to get a free scan and learn more about Spider SiteScan? Book a discovery call with our team today!



















